
The secret behind the solution
There are many well-proven authentication solutions in the market. But the absolute majority of services are still using static passwords for login, followed by repeated frauds and scandals.
So why continue on a dead end street? To make our connected world safe, it is about time to step up and do things in a different way.
With features like DeviceID, location, and a unique Risk Engine, the Keypasco Solution can raise the level of security for you and your customers. The groundbreaking technology even offers you a way to secure ALL of your customers without affecting the user experience – let us tell you how it works!

Security By Your Own Device!
Over the years, reports have been pouring in about leaked account information, stolen passwords, credit card fraud, and other troublesome and costly incidents, all due to poor security solutions.
By challenging traditions and making things easier and more adapted to human behaviour, we believe we can put an end to the problems. This is why we created the Keypasco Solution.
The Keypasco Solution began with a simple idea. We have all heard of fraudsters fooling people to give up their username and password. But, what if your username and password only worked on your own device? Then this type of fraud would disappear!
We then added location as a security factor, so you must not only have the right device, it must also be in the right place. Today Keypasco offers a unique patented security solution based on the end-user’s own device.
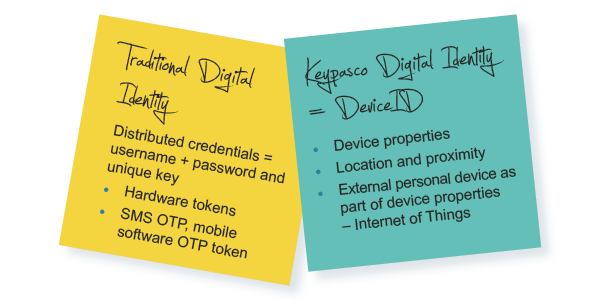
No distributed credentials = nothing to steal!
Traditionally ALL authentication solutions use distributed credentials, like password or a unique key, stored in a token or a mobile app.
But – credentials can, and will be stolen. That is why the patented Keypasco Solution does not rely on distributed credentials!

The Keypasco Solution
How it works
The solution consists of:
● The Keypasco server
● One or several devices
● A two-channel structure
● The Risk Engine
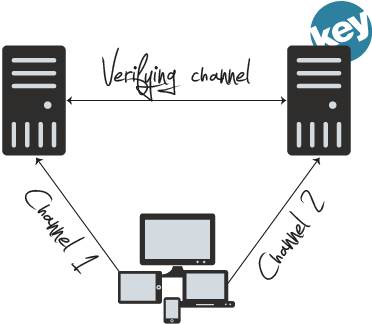
1. The DeviceID properties on the end-user’s device are scanned and stored at the Keypasco server. Any personal device may form part of the digital identity
2. The first channel sends information between the end-user’s device and the service provider
3. The second channel sends information between the end-user’s device and the Keypasco server
4. To verify the authentication the service provider checks with the Keypasco server to confirm:
● Device authentication
● Geographical location
● Proximity
● Risk Engine analysis
5. Then, it is decided whether the authentication is successful or not
Our patented features
● DeviceID and two-channel authentication: Bring the user’s own device as unique authentication device through a two-channel structure. Security by Your own device!
● Proximity: The user’s own devices / wearables in close position to each other as unique identity to enhance security.
● Keypasco PKI Sign: A unique solution for PKI in a mobile device without the need for a Secure Element. By using Keypasco PKI Sign no private key is stored at any one place, but it is still PKI compliant, making the solution extremely safe.
● Dynamic URL: This allows for single sign-on with one single trusted security app linking multiple Internet content providers on one side and multiple ID providers on the other.














