Security By Your Own Device!
Security is an on-going problem for any company that uses a login for their services. Often we are stuck with inadequate existing solutions and it is easy to be discouraged by all the work involved with implementing a new one. But, by challenging the traditions and making things easier and more adapted to human behaviour we believe we can make the Internet a safer place. This is why we create the Keypasco products and services.
Internet (in)security – a huge problem
Over the years, reports have been pouring in about leaked account information, stolen passwords, credit card fraud and other troublesome and costly incidents, all due to poor security solutions. Why does it continue to happen when we all know how important good security is?
- Username and password – still the most common authentication solution
- Hardware tokens – can add to security but are expensive, difficult to roll-out and inconvenient
- Human behaviour – people use the same or similar password for all services
- Federated login – the use of Gmail or Facebook to open a new account at another site may be convenient, but also very vulnerable
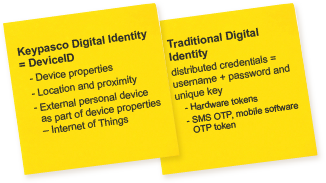
Traditionally ALL authentication solutions use distributed credentials, like password or a unique key stored in a token or a mobile app. But – credentials can be stolen. So why continue on a dead end street?

The solution that make sure that your username and password only works on your devices!
The unique Keypasco solution:
- Software based solution
- Convenient, low cost, easy for mass rollout
- Privacy/Integrity protection – no connection between Personal Identity and Digital Identity
- Evolving risk engine, for continuous improvement of your security
- Flexible and self-scalable to handle any volume
- On premises or Cloud service
- No distributed credentials – nothing to steal!

Keypasco mitigates threats
Phishing – by linking the users DeviceID with its geographical location, your username and password only works on your devices in the right locations.
Man in the Middle (MitM) and Man in the Browser (MitB) attacks – by Keypasco’s two-channel structure and Out of band secure notifications.
Malicious Virus Control (Viruses, Trojans, etc.) – with an Out of Band secure notifications we can stop them from taking control or replicate an end user’s device.
Theft/Robbery of a device can compromise a user’s security. With the Keypasco proximity feature, a user’s account is safe even if a device is stolen.

The unique Keypasco Solution:
Traditional solutions for online authentication stores personal information such as name, ID number, photo, phone number, email address, home address, account numbers and credit card numbers in databases, Keypasco do not collect nor store this type of information.
In addition, your traditional Digital ID consists of Password and Key = Distributed credentials. And credentials can, and will be stolen.
The Keypasco solution provides you with your own Digital Identity based on your Device properties, location and proximity to any external device you chose to be a part of your device properties.
With our DeviceID solution, there are no distributed credentials to be stolen!

Patented and award winning
Keypasco holds several patents that are granted in most of the world’s leading IT-nations such as Korea, Japan, China, Taiwan, European Union, Singapore and the United States.
Our prizes and awards are further proof of how innovative the Keypasco solution is.


The new road to Internet Security
The core technology of the Keypasco solution, the collecting of device-related data - makes it possible for us to offer something no one else does – a risk-based authentication solution that is easy to integrate and can be rolled out in the background to ALL end-users at once with instant impact, regardless of the number of users.
Service on your terms
Our aim is to provide our customers with the best security solution and service for their needs. We work globally through established local partners – as reseller and for local support.
Generic enrolment
We have learned that the enrolment process can be difficult. No one wants to bother the end-user with complicated procedures, even if it is to increase security. To solve this, we offer a way to associate devices without affecting the end-user.
In the majority of cases, it is the right account owner who logs in to an online service. By associating the account to the first device used to access the service, the account can be locked and then only accessible to that user from this specific device. In cases where an incorrect user locks an account, there was already a problem.
Now, with their account locked, the correct user is likely to contact you to resolve the issue. Over time, all cases will be resolved and fraud will go down. This is a way to enrol your existing customers with a minimum of end-user involvement.
Strict enrolment
Certain types of services may require an extra high level of security. It may for example be appropriate with a stricter enrolment for services such as: Finance, e-Government, credit card protection, and Mobile Payment services. We then apply a stricter enrolment with user identification.