
Cyberattacks and password breaches are now everyday news. But the passwordless era is here, bringing safer, faster, and more convenient ways to protect your digital world. Fingerprint scans, Face ID, Passkeys, and NFC — passwordless tech is transforming online security.
Here’s what you need to know about how passwordless authentication works, why it’s taking off, and how it can keep you safer online.
Passwords have long protected our emails, social media, and bank accounts. But they are now a hacker’s favorite target. With data breaches happening almost daily, both users and companies find themselves caught in an exhausting cycle of creating, remembering, and frequently updating passwords, often with little success at keeping attackers out.
Just this June, over 16 billion account credentials were leaked, affecting Google, Apple, Facebook, Telegram, and even government services. No wonder the push for passwordless security is gaining momentum, leaving behind vulnerable, easily stolen passwords for seamless, secure logins.
Recent Major Password Breaches
The past year has seen a surge in large-scale password leaks, highlighting the growing risks of relying on traditional credentials:
- June 2025: 16 Billion Credentials Breached
In one of the largest breaches ever recorded, a database containing over 16 billion account credentials surfaced online. The leaked data came from 30 different datasets, affecting major platforms like Apple, Google, Facebook, Telegram, and more. Alarmingly, security experts confirmed that a significant portion of this data had never been exposed in previous leaks. - May 2025: 184 Million Passwords Exposed
Cybersecurity researcher Jeremiah Fowler discovered an unprotected online database containing around 184 million credentials. The data included login details for email accounts, social media platforms, gaming services, and even some government-related domains like .gov.
And these two incidents are just the tip of the iceberg for 2025. Other major breaches have included cyberattacks targeting hospitals in Taiwan and a record-breaking number of personal data leaks in Japan. The stolen information from these incidents often ends up for sale on the dark web, where it can be used for identity theft, online scams, and extortion attempts.
Why Go Passwordless?
Passwordless authentication isn’t just a trend. It’s the next step in digital security. Here’s why:
1. The Inherent Weakness of Passwords
Passwords have always been a weak link in cybersecurity. They’re easy to guess, often reused across multiple accounts, and frequently stored in insecure ways. A 2024 cybersecurity report revealed that a staggering 88% of web-based attacks involved stolen credentials.
Even worse, users tend to create simple, memorable passwords and reuse them across services. This habit makes them highly vulnerable to credential stuffing attacks, where hackers use stolen login details to try accessing other platforms like Facebook, Google, or even government services.
2. The Alarming Frequency of Massive Data Breaches
In June 2025, the world witnessed the largest login credential breach in history, with 16 billion usernames and passwords leaked. Security analysts discovered 30 separate data sets, most of which contained fresh, previously unreleased data. This followed another breach in May 2025, which exposed 184 million records.
Stolen credentials don’t just sit idle. They’re sold on the dark web for identity theft, online scams, blackmail, and even corporate espionage, allowing attackers to infiltrate company networks and steal sensitive data.
3. Industry and Government-Led Transformation
Recognizing the growing risks, major international organizations and tech giants are leading the charge for passwordless authentication. Groups like the FIDO Alliance and W3C have developed global standards like WebAuthn and FIDO2 to support password-free security.
Tech leaders including Google, Apple, and Microsoft have already integrated passwordless solutions like Passkeys and Windows Hello into their services. Additionally, regulations like the EU’s PSD2 directive and other national security frameworks now require stronger, multi-factor authentication (MFA), further accelerating the shift to passwordless technology.
It’s not just about convenience, it’s a smarter, safer way to protect your data in today’s digital world.
How Does Passwordless Authentication Work?
Passwordless authentication eliminates the need to remember, or reuse traditional passwords. Instead, it relies on methods that are either physically unique to the user or tied to a secure device, dramatically reducing the risk of credential theft. Here are the most common approaches:
1️. Biometric Authentication
Biometrics use unique physical characteristics for identity verification. It’s fast, intuitive, and increasingly secure.
- Fingerprint Scanning: Widely adopted on smartphones and laptops, offering quick, natural, and highly reliable security.
- Facial Recognition: Technologies such as Apple Face ID and Windows Hello allow for rapid authentication. Modern systems have advanced to resist so-called photo attacks, where attackers try to trick facial recognition by using high-resolution printed images or displaying photos on a screen.
- Iris and Retina Scanning: Recently, OpenAI’s World App introduced iris-based identity verification using their ORB device, now available in Taiwan. While highly secure, iris data is considered to be sensitive biometric information and subject to strict privacy regulations in many countries.
- Other Biometric Methods: Emerging techniques include voice recognition, palm vein scanning, and even gait analysis, which may play a larger role in future security systems.
2️. Cryptographic Keys & Public-Private Key Systems
This method uses a pair of mathematically linked keys:
- Public Key: Shared openly and typically used to encrypt data.
- Private Key: Stored securely on the user’s device and used to decrypt data or verify identity.
Standards like WebAuthn and FIDO2 enable devices to generate and securely store private keys locally. Users can then verify their identity through a biometric scan or PIN code without transmitting sensitive credentials.
3️. Trusted Device-Based Verification
Authentication can also be tied to a device you physically own, adding a powerful extra layer of protection.
- Hardware Security Keys: Devices like YubiKey (via USB or NFC) offer phishing-resistant, hardware-based security compliant with FIDO2.
- NFC Devices: Smart cards or smartphones equipped with Near Field Communication (NFC) technology can instantly authorize logins by proximity.
- Authorization Apps: Some services, like Keypasco, send real-time authentication requests to a trusted device. The user must confirm the login attempt or enter a one-time passcode (OTP) displayed in the app, adding a secure, user-controlled checkpoint to the process.
The Current State and Future of Passwordless Adoption
The passwordless movement is gaining serious momentum, driven by tech giants, government initiatives, and growing user awareness. Here is how the landscape is evolving:
Major Tech Companies Are Leading the Way
- Microsoft now defaults to passwordless options for new accounts, promoting passkeys, push notifications, and hardware security keys instead of traditional passwords. They’ve even rebranded “World Password Day” to “World Passkey Day” to reflect this shift.
- Google and Apple have supported passkeys since 2022, integrating them into trusted device ecosystems and enabling seamless cloud-based key synchronization across browsers and platforms.
Government Support Is Accelerating Adoption
Governments are embracing passwordless authentication to improve public sector security:
- In the UK, both the government and National Health Service (NHS) plan to fully deploy passkeys across public services and government systems by the end of 2025. The UK’s National Cyber Security Centre (NCSC) has called this initiative “the beginning of the end for passwords.”
- According to the FIDO Alliance, awareness is growing fast:
- 74% of respondents are now familiar with passkeys
- 69% have used at least one passkey account
- 38% actively choose passkeys for logins whenever possible
Passwordless in Business and Commerce
Enterprise adoption is also delivering real-world benefits. Reports from companies such as Descope reveal that after implementing passkeys:
- Password reset requests dropped sharply
- Fraud attempts decreased
- Online conversion rates improved
- IT management became more efficient
The FIDO Alliance further reports that 48% of the world’s top 100 websites now support passkeys — more than double the figure from 2022.
Passwords are finally being replaced by safer, faster, and phishing-proof authentication. With major tech companies, governments, and enterprises moving toward passwordless solutions, the benefits are becoming clear:
🔐 Stronger security foundations — no more passwords to steal, reuse, or compromise.
⚡ Smoother user experiences — faster, hassle-free logins without typos or resets.
💸 Lower hardware and support costs — fewer password resets and better operational efficiency.
📈 Greater compliance and market competitiveness — stay ahead of regulations and strengthen brand trust.
The passwordless revolution is real. It is a necessary response to rising data breaches, phishing, and ransomware. In a world where digital safety has become a top priority for everyone, passwords are quietly fading into history.
Are you ready to leave passwords behind? The future is passwordless. Don’t get left behind.
Keypasco MFA
Keypasco MFA, developed by Lydsec Digital Technology, is a multi-factor authentication solution that integrates FIDO2 and FIDO UAF standards to provide a secure, passwordless login experience.
- Built on the global FIDO2 standard, it significantly reduces the burden of password management.
- Combines passwordless authentication with multiple verification factors, including device fingerprinting, geolocation, and biometric technologies, providing an enhanced level of security.
- Enables quick and secure device migration using NFC-enabled devices for seamless transfer of authentication credentials.
With Keypasco MFA, only authorized users can log in from registered devices at specific times and locations. The system employs a patented dual-channel authentication architecture that separates login and authentication encryption channels.
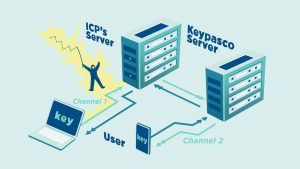
This design effectively blocks man-in-the-middle (MiTM) attacks, browser-in-the-middle (MiTB) attacks, phishing scams, and account takeover (ATO) attempts.













