
Two TSMC engineers tried leaking 2nm chip data in a Starbucks. This breach shows why companies must strengthen access control to protect sensitive information from insider threats.
TSMC 2nm Secret Leak: What Happened?
In late July 2025, Taiwan Semiconductor Manufacturing Company(TSMC) was rocked by a major insider threat.
Internal monitoring flagged short, suspicious logins—each under three minutes—accessing top-secret 2nm chip files. Investigators quietly tracked and caught two engineers red-handed at a Starbucks near HQ.
The investigation revealed a larger scheme. The stolen files had been passed to a former TSMC engineer—now employed by Japanese chip equipment giant Tokyo Electron (TEL). Leveraging remote work loopholes, the ex-employee recruited multiple insiders, including engineers with access to pre-production and R&D data. Over the course of a year, they used mobile phones to secretly photograph thousands of pages of confidential 2nm process documentation.
In total, nine individuals were implicated. Three engineers, directly involved in photographing sensitive data, were terminated immediately. The other six, primarily from the R&D team, were reassigned due to lesser involvement.
Under Taiwan’s National Security Act, technologies related to sub-14nm processes, AI chips, and third-generation semiconductors are designated “national core critical technologies.” Leaking such information is economic espionage and is punishable by up to 12 years in prison and a fine of up to NT$100 million (approx. USD 3 million). Three of the engineers are currently in detention, pending further legal proceedings.
Tokyo Electron fired the involved employees, affirmed a zero-tolerance policy, and pledged cooperation with authorities.
When Employee Accounts Leave the Building, Does Your Security Go With Them?
What makes the TSMC incident especially alarming is that it wasn’t caused by hackers, malware, or a database breach. It happened through a “legitimate” login.
The engineers used company-issued laptops and accounts. On the surface, everything appeared normal. But behind the scenes, they were accessing and misusing sensitive data—outside the office, in unauthorized environments.
This is one of the most difficult gray areas for modern companies to defend against.
When cybersecurity still relies solely on passwords or SMS-based authentication, a user account becomes a master key. No matter where the person is logging in from—at home, in a coffee shop, or even overseas—they can access the same sensitive systems, as long as the credentials are correct.
MFA Can Stop Hackers—But What About Insider Threats?
To strengthen cybersecurity, many organizations have adopted Multi-Factor Authentication (MFA), using combinations like:
- Username + password
- One-time passcodes via SMS or email
- Authenticator apps like Google Authenticator
These methods are highly effective at blocking external threats like hackers or bots. But they often fall short when the threat comes from within.
Why? Because most MFA systems are designed to confirm who you are—not where you are, what device you’re using, or whether your behavior is suspicious.
In other words, if a user has the correct password and verification code, the system grants access—whether they’re logging in from the company HQ, their living room, or a public coffee shop.
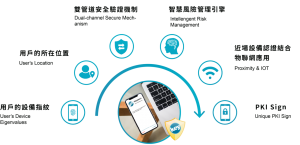
Don’t Let Accounts Become Universal Keys—Add Location and Device Intelligence
Unlike traditional MFA, context-aware multi-factor authentication takes a more intelligent approach. It doesn’t just ask, “Who are you?”—it also asks:
- Where are you logging in from?
- Are you using a trusted device?
- Is this behavior consistent with your usual patterns?
By analyzing location, device, and behavior, this approach greatly reduces the risk of account misuse—especially in an era where remote work and open offices are the norm.
If TSMC had used location-smart access controls, rogue logins from Starbucks would be blocked—credentials alone wouldn’t be enough.
Keypasco MFA takes this one step further by binding user accounts not just to verified devices, but also to approved geographic locations. Unless a login attempt comes from both a trusted device and a trusted place, access is denied—adding a powerful layer of protection beyond just passwords and codes.
In today’s Zero Trust era, companies can no longer assume that anything inside their network is inherently safe.
Workforces are increasingly mobile. Sensitive data is accessed from everywhere—not just behind the corporate firewall.
To stay ahead of evolving insider threats like the TSMC case, organizations must move beyond traditional account-based authentication and adopt context-aware access controls.
Upgrading from identity verification to full contextual validation is the key to building real digital resilience.
👉 Upgrade your security—try Keypasco MFA today and stay one step ahead.













