
As cyber threats become more sophisticated and IT environments more complex, Zero Trust Architecture has emerged as the leading next-generation security strategy worldwide.
Traditional perimeter-based defenses assumed that everything inside the corporate network was trustworthy, while everything outside was not. In contrast, Zero Trust is founded on the principle of ‘Never trust, always verify.’ Every access request, internal or external, must undergo strict identity verification, risk assessment, and authorization.
This post explains what Zero Trust security means, its origins, core technologies, and why it’s gaining global traction. It also highlights how Taiwan and other governments are promoting Zero Trust policies, and offers practical recommendations for businesses adopting this essential cybersecurity framework.
What Is Zero Trust Architecture?
Zero Trust is a cybersecurity framework that assumes no user, device, application, or network traffic is inherently trustworthy—not even those inside the corporate network. Every access request is dynamically verified and authorized based on real-time risk assessments, with even internal connections subject to multi-factor authentication (MFA) and continuous monitoring.
In 2020, the National Institute of Standards and Technology (NIST) released the NIST SP 800-207, defining Zero Trust as a strategy designed to prevent attackers from moving laterally within a network, stealing data, or disrupting systems.
Core Principles of Zero Trust:
- Verify and authorize every access request: Validate both user identity and device security posture for all requests, internal and external.
- Principle of least privilege: Users are granted only the minimum access necessary to perform their tasks.
- Micro-segmentation: The network is divided into smaller, isolated zones to limit lateral movement in case of a breach.
- Continuous monitoring and real-time risk assessment: All access behavior is constantly analyzed for anomalies, allowing rapid detection and response to potential threats.
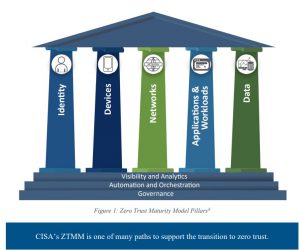
The Five Pillars of Zero Trust Architecture:
According to the CISA Zero Trust Maturity Model and the NIST SP 800-207, a complete Zero Trust framework is built around five core pillars:
- Identity
Ensure that every access request is thoroughly authenticated and authorized. This includes implementing multi-factor authentication (MFA), behavioral analytics, and continuous identity risk assessments. - Devices
Monitor and manage all devices accessing enterprise resources, ensuring they meet security standards such as updated OS versions, vulnerability patches, and active malware protection. Access permissions are adjusted based on the device’s current security status. - Networks
Implement micro-segmentation and grant only the minimal level of network access required for specific tasks, during specific times, and for specific data. Continuously monitor traffic for suspicious activity to prevent lateral movement attacks. - Applications and Workloads
Protect both internal and external applications, cloud services, and containerized workloads. This includes controlling application access permissions, securing APIs, and monitoring application behavior for anomalies. - Data
Classify and encrypt sensitive data, apply strict access controls, and enforce security policies throughout the data lifecycle — from storage to transmission and usage. Track and audit any unusual access behavior to maintain full data traceability.
Why Traditional Cybersecurity Is No Longer Enough
The 2024 Verizon Data Breach Investigations Report shows that account misuse, credential theft, and insider privilege abuse remain among the top causes of security incidents worldwide. This demonstrates that traditional perimeter-based models which focus on securing the network’s outer edge are no longer effective against modern threats such as insider attacks and lateral movement. Today’s enterprise IT environments are increasingly cloud-based, mobile-driven, and remote-friendly. As a result, legacy security tools like VPNs and firewalls can no longer fully protect all corporate resources and endpoints. Organizations are struggling with fragmented access control and a lack of network visibility, leaving critical security gaps.
To combat these challenges, the U.S. government issued the Executive Order 14028 in 2021, requiring all federal agencies to implement Zero Trust architecture. This directive set a powerful example for businesses worldwide, emphasizing the urgent need for modern cybersecurity strategies built on identity verification, multi-factor authentication (MFA), end-to-end encryption, and centralized incident response systems.
As businesses face increasingly sophisticated cyber threats, adopting a Zero Trust security framework is no longer optional. It’s a necessity for protecting sensitive data, cloud resources, and remote work environments.
Government Regulations Driving Zero Trust: Taiwan and Global Trends
Taiwan’s Progress on Zero Trust Implementation
In 2021, Taiwan’s Executive Yuan (Cabinet) introduced the National Information and Communication Security Development Program (2021–2024), aiming to proactively counter emerging cyber threats through advanced technologies. As part of the initiative, the newly established Ministry of Digital Affairs and Administration for Cyber Security were tasked with promoting Zero Trust within the public sector.
The program prioritized high-level government agencies as early adopters. By the end of 2024, 47 key agencies had received guidance and successfully implemented identity authentication mechanisms, a core component of Zero Trust architecture, to build a more secure and resilient network environment.
In addition, Taiwan launched a Zero Trust IoT Security Promotion Project to encourage industries to build Zero Trust-based demonstration environments for IoT (Internet of Things). The initiative offers financial incentives to supply chain vendors that integrate Zero Trust practices into their IoT cybersecurity efforts.
Taiwan’s Financial Supervisory Commission (FSC) has also taken steps to strengthen cybersecurity in the financial sector. In 2022, it released the Financial Cybersecurity Action Plan 2.0, naming Zero Trust as a key strategy. This was followed in 2024 by a dedicated Zero Trust Framework Guideline for Financial Institutions, which promotes best practices like identity verification, device health checks, and network segmentation to enhance cyber resilience in the industry.
Global Developments in Zero Trust Policy
The United States has taken a global lead in integrating Zero Trust into its national cybersecurity strategy. In 2021, President Biden signed Executive Order 14028: Improving the Nation’s Cybersecurity, mandating that all federal agencies adopt Zero Trust architecture. The Cybersecurity and Infrastructure Security Agency (CISA) and the Office of Management and Budget (OMB) were designated to define implementation roadmaps and technical standards.
In 2022, OMB issued Memorandum M-22-09, requiring all federal agencies to meet Zero Trust goals by the end of 2024. In 2023, CISA released the updated Zero Trust Maturity Model v2.0, which clearly defines the five foundational pillars and outlines three maturity levels. This model has since become a global reference for governments and enterprises alike seeking to adopt Zero Trust security.
Other governments around the world are also making Zero Trust security a national priority. Countries like Singapore, the United Kingdom, and Australia have integrated Zero Trust principles into their latest national cybersecurity strategies:
- Singapore’s Cybersecurity Strategy 2021
- The UK’s National Cyber Strategy 2022
- Australia’s Cyber Security Strategy 2023–2030
These frameworks designate Zero Trust as a key approach for securing government systems and critical infrastructure. Their policies mandate that government agencies and critical service providers adopt essential Zero Trust practices such as:
- Continuous identity verification
- Multi-factor authentication (MFA)
- The principle of least privilege
- Network micro-segmentation
- Anomaly detection and real-time threat response
By requiring these measures, these governments aim to strengthen defenses against increasingly sophisticated cyberattacks and protect sensitive national data and public services from potential disruption.
How Businesses Can Gradually Implement a Zero Trust Architecture
For businesses looking to adopt Zero Trust architecture, it’s important to tailor the implementation process to your organization’s size, existing infrastructure, and cybersecurity maturity. Rather than attempting an overnight overhaul, companies should set phased goals and follow a structured, step-by-step approach. Here’s a recommended roadmap:
1️⃣ Inventory and Manage Identities & Devices
Start by using Identity and Access Management (IAM) systems and endpoint security tools like EDR (Endpoint Detection and Response) and MDM (Mobile Device Management) to inventory all users, devices, and applications within your environment. This visibility is essential for identifying potential vulnerabilities.
The NIST SP 800-207 framework recommends unifying identity verification systems and enforcing multi-factor authentication (MFA) across the board. Weak passwords and shared accounts should be eliminated as a priority.
2️⃣ Implement Micro-Segmentation and Behavior Monitoring
Divide your network into smaller, secure zones based on business functions and application sensitivity. This helps prevent lateral movement attacks in the event of a breach.
Complement this with User and Entity Behavior Analytics (UEBA) and Security Information and Event Management (SIEM) platforms to continuously monitor for abnormal access patterns.
Additionally, consider replacing traditional VPNs with a Zero Trust Network Access (ZTNA) model, which only grants verified and authorized identities access to specific applications and resources.
According to the Gartner 2023 Market Guide, enterprise interest in micro-segmentation and ZTNA is accelerating. It’s projected that by 2026, over 60% of global enterprises will have adopted ZTNA to replace legacy VPN solutions.
3️⃣ Adopt Passwordless FIDO Authentication
A move toward FIDO (Fast Identity Online) passwordless authentication standards to reduce phishing attacks and credential theft risks. Leading global cloud and SaaS providers, including Google, Microsoft, and Okta, have already widely implemented passwordless logins, setting a strong precedent for enterprise adoption.
Conclusion: Zero Trust Is the Future of Modern Cybersecurity
As cyberattacks grow more sophisticated and traditional network perimeters vanish, legacy security models can no longer defend against lateral movement, credential misuse, and insider threats.
Zero Trust architecture addresses these challenges by enforcing a “never trust, always verify” approach. Through the integration of multi-factor authentication (MFA), Zero Trust Network Access (ZTNA), network micro-segmentation, data classification, and continuous behavior monitoring, organizations can build a dynamic, adaptive defense system that reduces their attack surface and limits the impact of potential breaches.
Around the world, both governments and large enterprises are making Zero Trust a core component of their long-term cybersecurity strategies. Businesses that proactively inventory their digital assets, implement IAM, ZTNA, FIDO passwordless authentication, and micro-segmentation — while gradually building out the five pillars of Zero Trust — will significantly strengthen their resilience against ransomware, advanced persistent threats (APTs), and credential leaks.
By embracing Zero Trust early, companies can better protect critical operations and ensure business continuity in the face of evolving cyber risks.
Keypasco ZTNA
Keypasco ZTNA is a cybersecurity solution built on Zero Trust Network Access principles. Developed in line with U.S. NIST and CISA standards, as well as Taiwan’s government Zero Trust framework, it is certified by the National Institute of Cyber Security. Keypasco ZTNA employs identity verification, device authentication, and trust inference technologies to help organizations achieve comprehensive and robust cybersecurity protection.
- Identity Verification: Offers multi-factor authentication, including FIDO U2F and FIDO2 solutions.
- Device Authentication: Scans device attributes and software information, storing them on Keypasco servers for device validation.
- Trust Inference: Uses artificial intelligence to analyze behavior, continuously assess risk, and trigger additional authentication when needed.
Keypasco not only meets international standards and real-world demands, but is trusted by government agencies, financial institutions, healthcare providers, smart buildings, and high-tech industries worldwide. As cyber threats evolve, we remain committed to empowering organizations with robust, future-ready security solutions. This ensures that they stay compliant, resilient, and ahead of the curve in a rapidly changing digital landscape.













