
A major data breach at Qantas has exposed the personal information of 6 million customers after hackers compromised a third-party support system. This incident highlights why Multi-Factor Authentication (MFA) and Zero Trust security are now essential for protecting your data.
Major Data Breach at Qantas Airways
On July 1, 2025, Qantas Airways confirmed a large-scale data breach affecting approximately 6 million customers. Hackers targeted a third-party customer service platform used by the airline, compromising personal details including names, email addresses, phone numbers, dates of birth, and frequent flyer numbers. Fortunately, no credit card details, passport numbers, passwords, or account PINs were stored on the platform and remained secure.
Qantas’ IT security team detected suspicious activity on June 30 and immediately isolated the affected platform, ensuring that core operations and flight safety were not impacted.
Following the incident, Qantas CEO Vanessa Hudson issued a public apology and reported the breach to the Australian Cyber Security Centre (ACSC), the Office of the Australian Information Commissioner (OAIC), and the Australian Federal Police (AFP).
According to multiple reports, the FBI recently warned about the hacking group “Scattered Spider” (also known as UNC3944), which has been actively targeting airline companies. This group is notorious for using social engineering tactics, impersonating customer service staff to bypass 2FA protections, hijacking SIM cards, and intercepting authentication codes to infiltrate corporate systems.
Although no financial information or passwords were leaked in this incident, the stolen personal data still poses a serious risk of phishing attacks, identity theft, and potential misuse of frequent flyer points. The breach has reignited concerns about the cybersecurity resilience of Australian businesses, especially following recent high-profile incidents at Optus, Australia’s second-largest telecom provider, and Medibank, the country’s largest private health insurer, which have already prompted calls for stricter cybersecurity regulations.
The Real Risks Behind Data Leaks
When news of a data breach breaks, many people tend to shrug it off, thinking:
“Well, at least they didn’t get my credit card number — I should be fine.”
But the reality is far more concerning. When news of a data breach breaks, many people shrug it off, thinking, “Well, at least they didn’t get my credit card number—I should be fine.” The reality, however, is far more concerning.
Even seemingly harmless personal details like your name, date of birth, phone number, and email address can become valuable tools in the hands of hackers. These details are often used in phishing scams, identity theft, and social engineering attacks designed to manipulate victims and compromise their accounts.
Here’s how leaked data is commonly exploited:
a. Targeted Phishing Emails/SMS
Cybercriminals use leaked information — such as your name, email address, and frequent flyer number — to craft emails that look convincingly legitimate, often posing as customer service representatives. These phishing messages might claim:
- There’s an issue with your account
- You have bonus points to redeem
- Your frequent flyer miles are about to expire
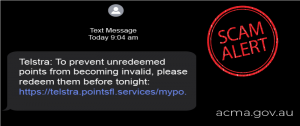
Source: ACMA
The goal is to trick victims into clicking malicious links or logging into fake websites to steal login credentials, credit card details, and other sensitive data.
b. Vishing: Phone Scams Posing as Customer Service
With access to leaked phone numbers and frequent flyer details, hackers may call victims pretending to be from the airline’s customer service department. These calls typically warn about flight disruptions or issues with loyalty points, then request personal details like passport numbers, verification codes, or even ask victims to link payment information — all under the guise of “identity verification.”
c. Identity Theft & Social Engineering
By combining leaked names, birth dates, email addresses, and phone numbers, cybercriminals can launch highly targeted identity theft and social engineering attacks. Common tactics include:
- Hacking into personal accounts and resetting passwords
- Applying for loans or credit cards using stolen identities
- SIM swapping attacks
These schemes have surfaced repeatedly in past data breaches, often leading to unauthorized account activity, financial loss, and victims discovering the damage only after it’s too late.
What Should You Do If Your Data Was Exposed?
If you’re a Qantas frequent flyer or have recently registered on their customer service platform, it’s important to take immediate precautions to protect your personal information:
- Change your email and important account passwords — especially for services connected to your travel, banking, or online shopping accounts. This prevents hackers from using leaked data for credential-stuffing attacks.
- Enable Multi-Factor Authentication (MFA) on all critical accounts. This adds an extra layer of protection, particularly for loyalty programs, financial services, and flight booking platforms.
- Be cautious of unexpected calls and emails. If someone contacts you claiming to be from Qantas or your bank, never follow instructions directly from the caller. Instead, hang up and call the official customer service number to verify the request.
Even if your name isn’t on the affected customer list, it’s wise to proactively monitor your account activity and login records. With the rising number of data breaches and scams in recent years, staying vigilant is no longer optional — it’s essential.
Why MFA and Zero Trust Are Essential for Businesses
The Qantas breach highlights a crucial reality of modern cybersecurity: even when a company’s core systems are well-defended, a single compromised third-party platform or employee account can expose millions of records to cybercriminals on the dark web.
This incident is yet another reminder of why organizations must adopt the cybersecurity principle of Zero Trust — which operates on the philosophy of:
“Never trust, always verify.”
Under a Zero Trust model, no user, device, or service is automatically trusted, even if they’re already inside the corporate network. Every access attempt must be verified continuously, and sensitive data should be isolated behind multiple layers of protection, reducing the risk of lateral movement after a breach.
Why Multi-Factor Authentication (MFA) Matters
Multi-Factor Authentication (MFA) adds a critical extra layer of protection by requiring multiple forms of identity verification — typically combining something you know (like a password), something you have (like a one-time passcode or security key), and something you are (like a biometric check).
Even if a hacker manages to steal your login credentials, breaching a second or third layer of authentication is significantly more difficult.
Groups like Scattered Spider are notorious for using social engineering tactics to obtain one-time passcodes from victims. As a result, relying solely on SMS-based verification is no longer considered secure.
Recommended Best Practices:
- Disable SMS-based two-factor authentication (2FA) wherever possible
- Implement app-based authentication codes or security keys for all user accounts
- Enforce hardware security keys for administrators and high-privilege accounts
Keypasco’s Multi-Factor Authentication (MFA), developed by Lydsec Digital Technology, is a multi-factor authentication solution that integrates FIDO2 and FIDO UAF standards to provide a secure, passwordless login experience.
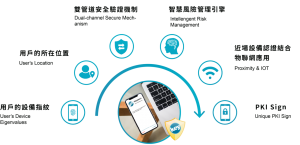
- Built on the global FIDO2 standard, it significantly reduces the burden of password management.
- Combines passwordless authentication with multiple verification factors, including device fingerprinting, geolocation, and biometric technologies, providing an enhanced level of security.
- Enables quick and secure device migration using NFC-enabled devices for seamless transfer of authentication credentials.
With Keypasco MFA, only authorized users can log in from registered devices at specific times and locations. The system employs a patented dual-channel authentication architecture that separates login and authentication encryption channels. This design effectively blocks man-in-the-middle (MiTM) attacks, browser-in-the-middle (MiTB) attacks, phishing scams, and account takeover (ATO) attempts.
What Is Zero Trust Network Access (ZTNA)?
Zero Trust is a modern cybersecurity strategy built on the principle:
“Never trust, always verify.”
Key concepts include:
- No device, user, or application is trusted by default
- Every access request requires identity verification, behavior monitoring, and risk assessment
- Access permissions are dynamically adjusted based on real-time risk
This means everyone — employees, contractors, vendors — must undergo strict verification and follow the principle of least privilege, preventing attackers from moving laterally after breaching one layer.
「Keypasco ZTNA」is a cybersecurity solution based on the Zero Trust Network Access. The product is developed with reference to standards from the U.S. NIST and CISA, as well as Taiwan’s government Zero Trust technical framework. It is certified by the National Institute of Cyber Security and employs identity verification, device authentication, and trust inference technologies to help enterprises and public/private sectors provide comprehensive and robust cybersecurity protection.
- Identity Verification: Offers multi-factor authentication, including FIDO U2F and FIDO2 solutions.
- Device Authentication: Scans device attributes and software information, storing them on Keypasco servers for device validation.
- Trust Inference: Uses artificial intelligence to analyze behavior, continuously assess risk, and trigger additional authentication when needed.
Keypasco not only meets international standards and real-world demands, but is trusted by government agencies, financial institutions, healthcare providers, smart buildings, and high-tech industries worldwide. As cyber threats evolve, we remain committed to empowering organizations with robust, future-ready security solutions. This ensures that they stay compliant, resilient, and ahead of the curve in a rapidly changing digital landscape.













